getnametag.com
Stop social engineering attacks with identity verification

AI Project Details
Secure Your Helpdesk with Nametag: The Ultimate Defense Against Social Engineering
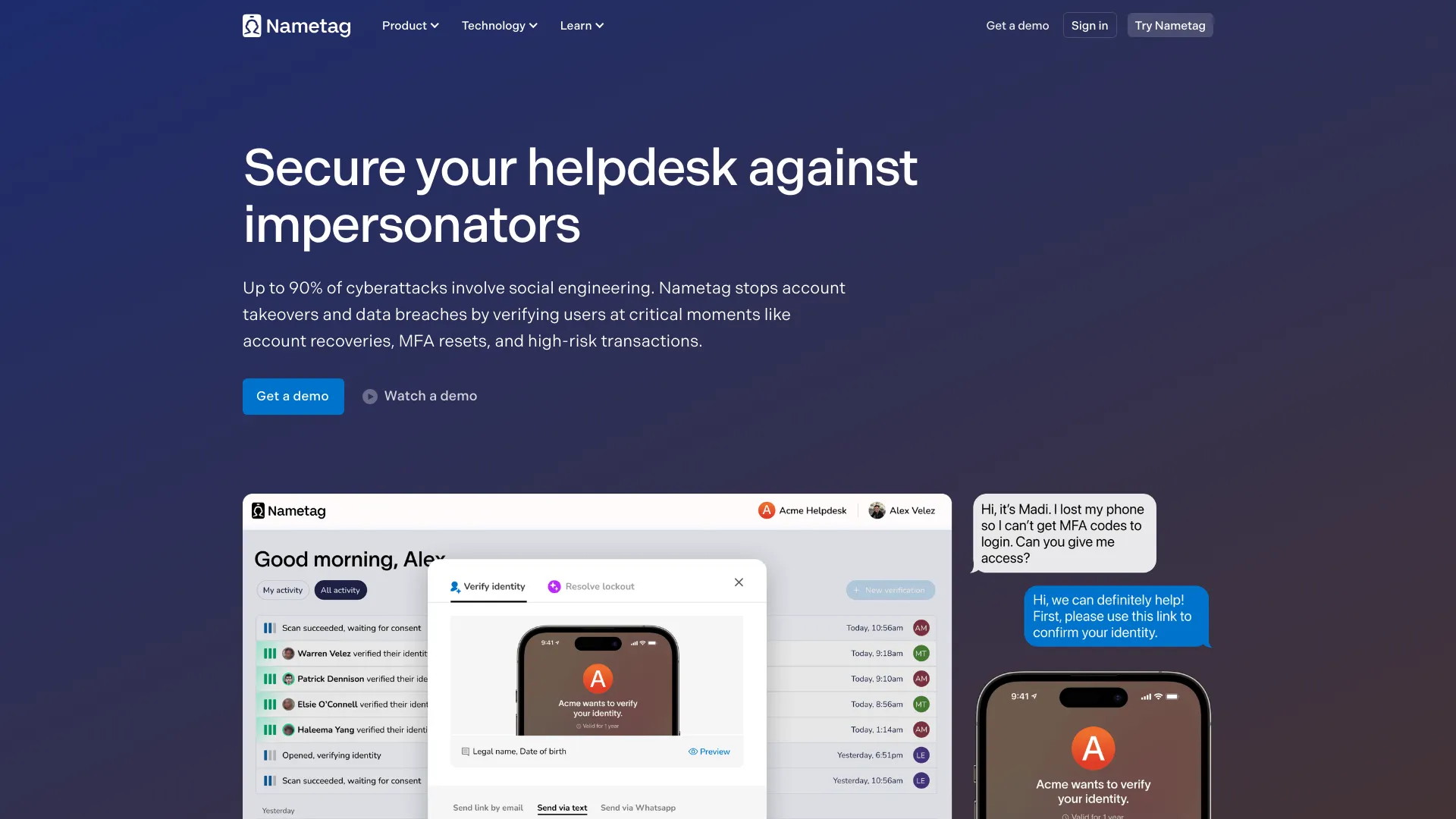
In an era where cyberattacks are increasingly targeting the human element, Nametag provides a robust, automated solution to stop social engineering in its tracks. Traditional security measures often fall short at the helpdesk, where sophisticated attackers use rapport and pressure to bypass security protocols. Nametag solves this by introducing cryptographically secure identity verification, ensuring that you always know exactly who is on the other end of the line.
Comprehensive Identity Verification Features
Nametag goes beyond simple passwords or SMS codes. It leverages advanced technology to provide a "Green Room" for identity, ensuring only authorized users gain access to sensitive systems. Key features include:
- Government ID Scanning: Instantly verify the authenticity of thousands of different types of government-issued IDs from around the world.
- Biometric Liveness Detection: Prevent deepfakes and photo-injection attacks using spatial biometric technology that ensures a person is physically present and matching their ID.
- Mobile-First Experience: Users can verify their identity in seconds using their own smartphones, removing the need for clunky hardware or complex software installations.
- Self-Service Account Recovery: Enable users to securely reset their own passwords or MFA tokens without human intervention, significantly reducing helpdesk ticket volume.
- Privacy-First Design: Nametag verifies identities without storing sensitive personal data, helping organizations maintain compliance with GDPR, CCPA, and other privacy regulations.
Key Use Cases for Enterprise Security
By integrating Nametag into your existing security workflow, you can secure the most vulnerable touchpoints in your organization:
- Stopping Helpdesk Impersonation: Prevent attackers from calling your IT support team to request fraudulent password resets or MFA bypasses.
- Secure Employee Onboarding: Verify the identity of new remote hires before granting them access to internal company resources and hardware.
- Privileged Access Management (PAM): Add a layer of biometric verification before allowing administrators to access sensitive databases or high-value infrastructure.
- MFA Resets: Securely re-enroll users into Multi-Factor Authentication systems after they lose their device, ensuring the request is legitimate.
The Benefits of Choosing Nametag
Implementing Nametag’s identity verification platform offers immediate ROI for IT and Security teams. By automating the verification process, organizations can reduce helpdesk costs, improve the user experience with faster resolution times, and virtually eliminate the risk of account takeover (ATO) attacks caused by social engineering.
Nametag integrates seamlessly with industry-leading Identity Providers (IdPs) like Okta, Microsoft Entra ID (Azure AD), and Ping Identity, allowing for a smooth deployment that enhances your existing security stack without disrupting employee productivity. Protect your organization from the next wave of identity-based threats with the world's most secure identity verification engine.